- DigestAuth
- Configuration Examples
- Configuration Options
- users
- usersFile
- realm
- headerField
- removeHeader
DigestAuth
Adding Digest Authentication
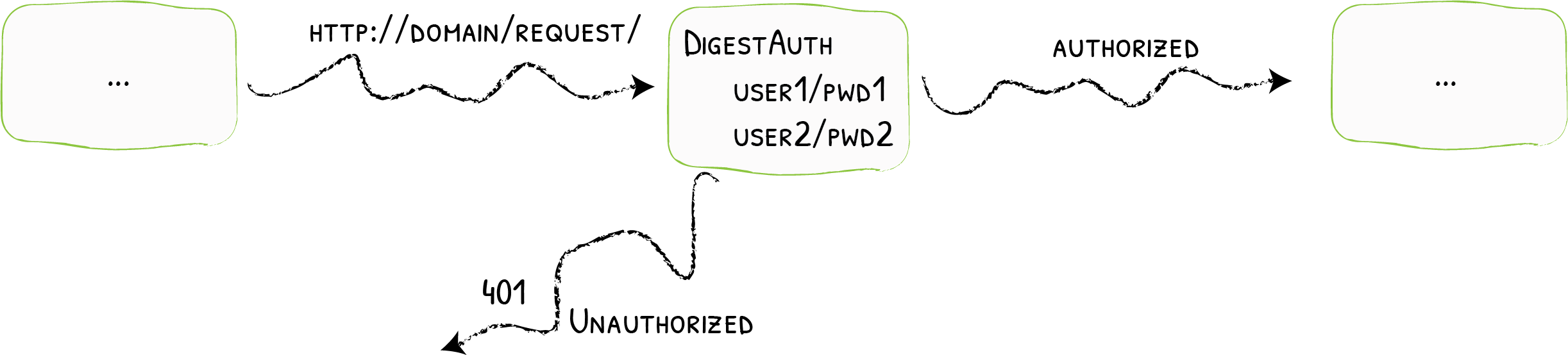
The DigestAuth middleware is a quick way to restrict access to your services to known users.
Configuration Examples
# Declaring the user listlabels:- "traefik.http.middlewares.test-auth.digestauth.users=test:traefik:a2688e031edb4be6a3797f3882655c05,test2:traefik:518845800f9e2bfb1f1f740ec24f074e"
# Declaring the user listapiVersion: traefik.containo.us/v1alpha1kind: Middlewaremetadata:name: test-authspec:digestAuth:secret: userssecret
"labels": {"traefik.http.middlewares.test-auth.digestauth.users": "test:traefik:a2688e031edb4be6a3797f3882655c05,test2:traefik:518845800f9e2bfb1f1f740ec24f074e"}
# Declaring the user listlabels:- "traefik.http.middlewares.test-auth.digestauth.users=test:traefik:a2688e031edb4be6a3797f3882655c05,test2:traefik:518845800f9e2bfb1f1f740ec24f074e"
# Declaring the user list[http.middlewares][http.middlewares.test-auth.digestAuth]users = ["test:traefik:a2688e031edb4be6a3797f3882655c05","test2:traefik:518845800f9e2bfb1f1f740ec24f074e",]
# Declaring the user listhttp:middlewares:test-auth:digestAuth:users:- "test:traefik:a2688e031edb4be6a3797f3882655c05"- "test2:traefik:518845800f9e2bfb1f1f740ec24f074e"
Configuration Options
Tip
Use htdigest to generate passwords.
users
The users option is an array of authorized users. Each user will be declared using the name:realm:encoded-password format.
Note
- If both
usersandusersFileare provided, the two are merged. The contents ofusersFilehave precedence over the values inusers. - For security reasons, the field
usersdoesn't exist for Kubernetes IngressRoute, and one should use thesecretfield instead.
labels:- "traefik.http.middlewares.test-auth.digestauth.users=test:traefik:a2688e031edb4be6a3797f3882655c05,test2:traefik:518845800f9e2bfb1f1f740ec24f074e"
apiVersion: traefik.containo.us/v1alpha1kind: Middlewaremetadata:name: test-authspec:digestAuth:secret: authsecret---apiVersion: v1kind: Secretmetadata:name: authsecretnamespace: defaultdata:users: |2dGVzdDp0cmFlZmlrOmEyNjg4ZTAzMWVkYjRiZTZhMzc5N2YzODgyNjU1YzA1CnRlc3QyOnRyYWVmaWs6NTE4ODQ1ODAwZjllMmJmYjFmMWY3NDBlYzI0ZjA3NGUKCg==
"labels": {"traefik.http.middlewares.test-auth.digestauth.users": "test:traefik:a2688e031edb4be6a3797f3882655c05,test2:traefik:518845800f9e2bfb1f1f740ec24f074e"}
labels:- "traefik.http.middlewares.test-auth.digestauth.users=test:traefik:a2688e031edb4be6a3797f3882655c05,test2:traefik:518845800f9e2bfb1f1f740ec24f074e"
[http.middlewares][http.middlewares.test-auth.digestAuth]users = ["test:traefik:a2688e031edb4be6a3797f3882655c05","test2:traefik:518845800f9e2bfb1f1f740ec24f074e",]
http:middlewares:test-auth:digestAuth:users:- "test:traefik:a2688e031edb4be6a3797f3882655c05"- "test2:traefik:518845800f9e2bfb1f1f740ec24f074e"
usersFile
The usersFile option is the path to an external file that contains the authorized users for the middleware.
The file content is a list of name:realm:encoded-password.
Note
- If both
usersandusersFileare provided, the two are merged. The contents ofusersFilehave precedence over the values inusers. - Because it does not make much sense to refer to a file path on Kubernetes, the
usersFilefield doesn't exist for Kubernetes IngressRoute, and one should use thesecretfield instead.
labels:- "traefik.http.middlewares.test-auth.digestauth.usersfile=/path/to/my/usersfile"
apiVersion: traefik.containo.us/v1alpha1kind: Middlewaremetadata:name: test-authspec:digestAuth:secret: authsecret---apiVersion: v1kind: Secretmetadata:name: authsecretnamespace: defaultdata:users: |2dGVzdDokYXByMSRINnVza2trVyRJZ1hMUDZld1RyU3VCa1RycUU4d2ovCnRlc3QyOiRhcHIxJGQ5aHI5SEJCJDRIeHdnVWlyM0hQNEVzZ2dQL1FObzAK
"labels": {"traefik.http.middlewares.test-auth.digestauth.usersfile": "/path/to/my/usersfile"}
labels:- "traefik.http.middlewares.test-auth.digestauth.usersfile=/path/to/my/usersfile"
[http.middlewares][http.middlewares.test-auth.digestAuth]usersFile = "/path/to/my/usersfile"
http:middlewares:test-auth:digestAuth:usersFile: "/path/to/my/usersfile"
A file containing test/test and test2/test2
test:traefik:a2688e031edb4be6a3797f3882655c05test2:traefik:518845800f9e2bfb1f1f740ec24f074e
realm
You can customize the realm for the authentication with the realm option. The default value is traefik.
labels:- "traefik.http.middlewares.test-auth.digestauth.realm=MyRealm"
apiVersion: traefik.containo.us/v1alpha1kind: Middlewaremetadata:name: test-authspec:digestAuth:realm: MyRealm
"labels": {"traefik.http.middlewares.test-auth.digestauth.realm": "MyRealm"}
labels:- "traefik.http.middlewares.test-auth.digestauth.realm=MyRealm"
[http.middlewares][http.middlewares.test-auth.digestAuth]realm = "MyRealm"
http:middlewares:test-auth:digestAuth:realm: "MyRealm"
headerField
You can customize the header field for the authenticated user using the headerFieldoption.
labels:- "traefik.http.middlewares.my-auth.digestauth.headerField=X-WebAuth-User"
apiVersion: traefik.containo.us/v1alpha1kind: Middlewaremetadata:name: my-authspec:digestAuth:# ...headerField: X-WebAuth-User
labels:- "traefik.http.middlewares.my-auth.digestauth.headerField=X-WebAuth-User"
"labels": {"traefik.http.middlewares.my-auth.digestauth.headerField": "X-WebAuth-User"}
[http.middlewares.my-auth.digestAuth]# ...headerField = "X-WebAuth-User"
http:middlewares:my-auth:digestAuth:# ...headerField: "X-WebAuth-User"
removeHeader
Set the removeHeader option to true to remove the authorization header before forwarding the request to your service. (Default value is false.)
labels:- "traefik.http.middlewares.test-auth.digestauth.removeheader=true"
apiVersion: traefik.containo.us/v1alpha1kind: Middlewaremetadata:name: test-authspec:digestAuth:removeHeader: true
"labels": {"traefik.http.middlewares.test-auth.digestauth.removeheader": "true"}
labels:- "traefik.http.middlewares.test-auth.digestauth.removeheader=true"
[http.middlewares][http.middlewares.test-auth.digestAuth]removeHeader = true
http:middlewares:test-auth:digestAuth:removeHeader: true
